1. TL;DR
The risk landscape for family offices is no longer defined by isolated threats – it’s shaped by convergence, speed, and complexity.
The following highlights capture the most pressing risk dynamics in 2025, drawn from frontline insights across cybersecurity, physical security, governance, and reputation. These are not future hypotheticals – they’re current realities shaping how families protect their assets, people, and legacy.
Cyber threats are more sophisticated, frequent, and specific
Powered by AI, targeting families through advanced social engineering, deepfakes, and exploiting third-party exposures. The financial and operational impacts are substantial and growing.
Physical risks are increasingly cyber-physical
Smart-home systems, travel tech, and IoT devices blur the lines, creating new vectors for intrusion and harm, including crypto-related kidnappings.
Geopolitical risk is a primary disruptor
Formerly stable regions face new volatility, impacting investments, supply chains, and physical safety through regulatory unpredictability and rising political violence.
Regulatory and governance risk is intensifying
As family offices are increasingly viewed as an “asset class”, they face growing regulatory scrutiny, while internal governance gaps around insider threats and vendor management persist.
Reputation can collapse in hours
AI-driven misinformation, sophisticated impersonation, and viral backlash are rising sharply in volume and velocity, demanding proactive narrative management.
OSINT is no longer optional
Open-source intelligence is a critical tool for both attackers and defenders, requiring active monitoring and mitigation of the family’s digital footprint.
Crisis readiness remains a significant gap
Most family offices still lack coordinated, documented, and tested crisis management plans capable of addressing complex, cascading incidents.
Risk maturity varies wildly
Some families now operate like resilient institutions, while others remain exposed by informality, inaction, and a mismatch in perceived versus actual preparedness.
This report aims to shift the conversation from protection to preparedness. From silos to systems. From reactive to resilient. Keeping reading for the full report.
We’d like to thank Crisis24 Private Strategic Group and Accordant Global Partners for their valued contribution and insight, in addition to the experts cited throughout. Special thanks also to David Struthers for his support.
 |
 |
2. Introduction
In today’s increasingly volatile global environment, family offices face a rapidly evolving landscape of interconnected risks. From cyberattacks and digital impersonation to physical intrusions, reputational threats, and geopolitical instability, 2025 has become a defining year for proactive security and risk governance. Building on the insights of the 2024 edition, this report provides a deep, structured look at the risks most relevant to private wealth owners and their trusted advisers. Simple’s latest poll data supports this expanded view. When asked about the biggest threats to long-term wealth continuity, families identified not just external shocks, but internal breakdowns in vision, responsibility, and trust.
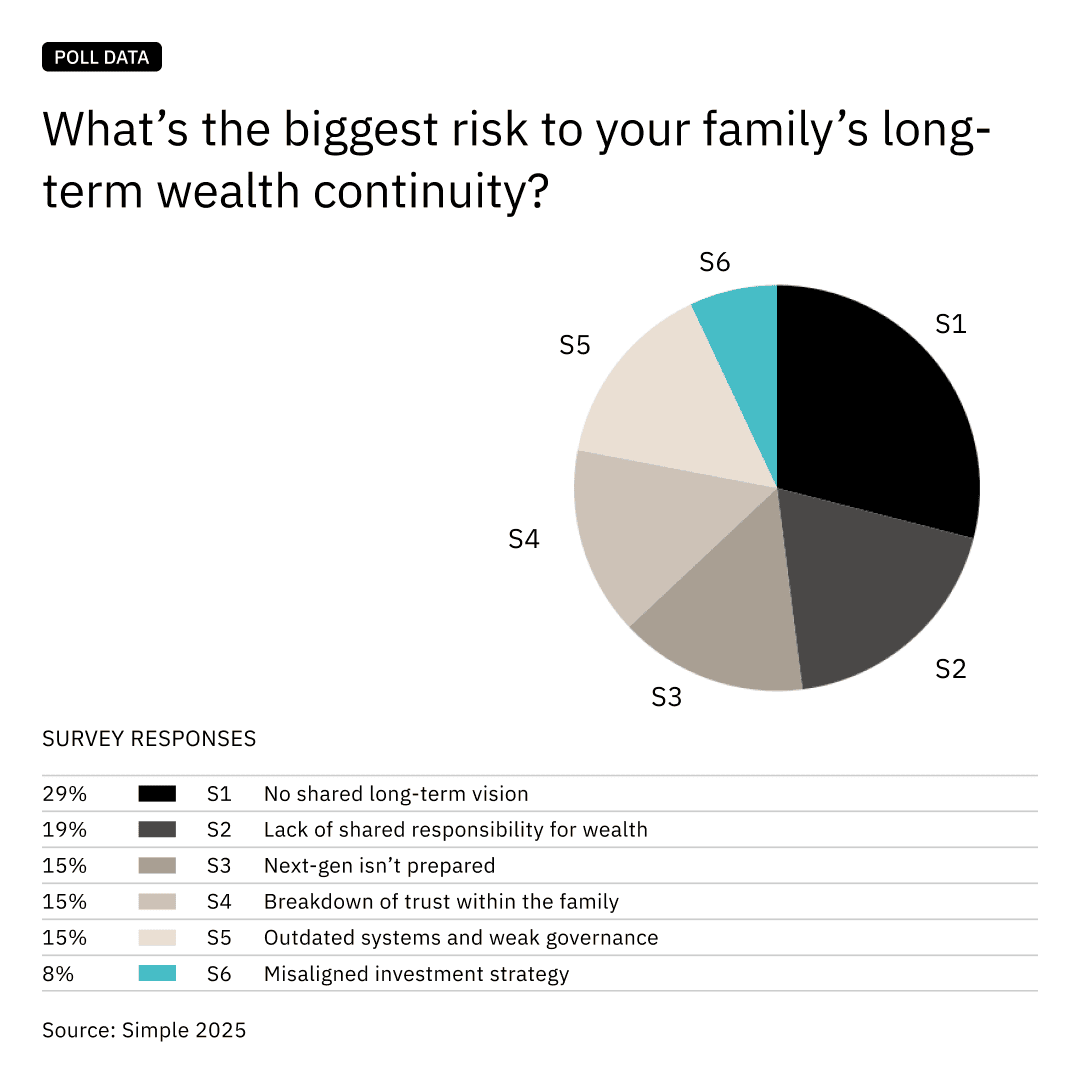
Families perceive lack of long-term vision and shared responsibility as top risks to sustaining wealth across generations.
This year, we have added new sections, expanded core areas, and worked closely with experts across cybersecurity, intelligence, reputation, and operations to ensure the recommendations are practical, current, and global in perspective. A key driver of this evolution is artificial intelligence (AI), which is transforming both the tools of attack – from deepfakes to hyper-personalised phishing – and the tools of defence, including threat detection, OSINT analysis, and crisis response. The data underpinning this report reflects a clear trend: threats are not only increasing in frequency but also in sophistication, demanding a more integrated and strategic approach to resilience.
For more on how complexity is reshaping UHNW needs, read The UHNWI of 2025.
To develop the 2025 edition, we gathered insight from risk and security experts across Simple’s network, professionals spanning cybersecurity, reputation, intelligence, physical protection, and operational resilience. We also ran a series of targeted polls across our family office readership to capture sentiment around emerging risks, preparedness, and internal blind spots.
The responses painted a vivid picture of an industry that is becoming more alert, but not uniformly prepared. Many are aware of the shifting risk landscape, but fewer have adapted their governance structures or incident playbooks to match. Several contributors described the current environment as a “grey zone” where threats often sit between digital and physical domains, or between perception and reality. The imperative for family offices is to move beyond awareness to actionable, embedded resilience.
One practitioner put it plainly:
“The biggest issue is not that the risk is new. It’s that families haven’t internalised what’s changed in the threat environment. It’s not just digital – it’s systemic.”
Throughout this report, you will find these practitioner insights woven into each section, along with reflections on what the data tells us about risk maturity in 2025. Our aim is not only to surface these risks but to illuminate how leading families and service providers are responding in practice.
The purpose of this report is threefold:
-
To map and contextualise the top security risks facing family offices in 2025.
-
To highlight how these risks are evolving across regions and technologies, supported by current data and expert analysis.
-
To offer actionable insights, case examples, and practitioner input to support better decision-making and foster a culture of proactive risk management.
This is not a checklist, it is a blueprint. One that brings together narrative, data, and guidance from those on the front lines of family office risk.
3. Cybersecurity

When Deepfakes Dial In
In early 2024, a European family office received a call that appeared to come from their principal, requesting a time-sensitive transfer to an overseas account. The voice sounded familiar. It matched previous voicemail recordings. But it was a deepfake – AI-generated audio mimicking the principal, backed by social engineering and data harvested from a breached travel booking service. The fraud was not caught until after the funds had cleared. And it was not an isolated case.
Strategic Context
Cybersecurity remains the single most urgent risk domain for family offices in 2025. This urgency stems not from the novelty of the threat, but from the dramatic evolution in its speed, specificity, and strategic complexity. The landscape has shifted significantly from 2024, with threat actors moving beyond brute-force methods to deploy AI-enhanced phishing, voice cloning, and highly targeted social engineering techniques.
These attacks are precision-crafted for the unique operational patterns and high-value nature of private wealth, making family offices, as Oriane Cohen, CEO of OC Strategic Advisory, notes, “juicy targets – high value, low visibility.” AI, she observes, “makes that scale possible“, transforming opportunistic attacks into bespoke campaigns.
The data underscores this heightened threat: globally, 43% of family offices reported experiencing a cyberattack in the last one to two years, a figure rising to 57% in North America. For larger offices (over $1 billion AUM), this jumps to 62%. Attacks are often persistent, with half of those affected enduring three or more separate incidents.
The financial ramifications are stark, with the global average cost of a data breach reaching $4.9 million in 2024, a 10% year-over-year increase, and one-third of attacked family offices suffering tangible loss or damage, commonly operational disruption or data loss (20% of victims) and direct financial loss (18%).
The attack surface has widened considerably as offices embrace distributed digital ecosystems, remote staff, and sometimes informal communication channels for critical decisions. Phishing remains the most prevalent vector (experienced by 93% of attacked offices), frequently manifesting as Business Email Compromise (BEC), while malware (35%) and broader social engineering (23%) follow.
The rise of Ransomware-as-a-Service (RaaS) models has lowered the barrier to entry for cybercriminals, leading to a surge in attacks often involving double or even quadruple extortion tactics. Morten Peachey, Chief Information Security Officer at coc00n, notes that these attacks are typically more focused on the “organisations surrounding UHNW families rather than the individuals or families themselves”. Furthermore, supply chain vulnerabilities are a growing concern, with predictions that 45% of organisations globally will face significant supply chain attacks by 2025.
Simultaneously, regulatory scrutiny is intensifying. New compliance regimes – including NIS2 and DORA in the EU, and enhanced SEC cyber disclosure rules in the US – demand faster reporting, greater transparency, and board-level accountability. This convergence of sophisticated threats, expanding vulnerabilities, and stricter regulations means cyber risk is no longer a siloed IT concern.
Its effects bleed into physical access systems, travel risks, insurance readiness, and reputation, firmly establishing it as a critical governance issue. Yet, a significant preparedness gap persists: a concerning 31% of family offices globally lack a cyber incident response plan (IRP), and only 26% claim to have a “robust” one. This is compounded by 63% lacking cybersecurity insurance and 68% not having adopted ‘Know Your Vendor’ (TPRM) protocols, despite experts highlighting ransomware, data breaches (often linked to OSINT), and deepfake-led attacks as key escalating threats.
Evidence & Indicators
- 78% of family office leaders now rank cyber as their top risk concern
- 43% report experiencing at least one cyber incident in the past 24 months (57% in North America, 62% for offices >$1B AUM)
- Only 26% have a tested, robust cyber incident response plan; 31% have no plan at all
- 70% of respondents in a Simple poll believe family offices are underestimating cyber exposure
- Just 12% have run a simulated cyberattack in the past year
- Common attack types include credential harvesting, business email compromise (BEC), AI-powered impersonation, and ransomware
- The global average cost of a data breach hit $4.88 million in 2024
- Despite 83% calling cyberattacks their biggest operational risk in one survey, only 22% ranked it as a top organisational risk for 2024
- A confirmed recent tactic includes ‘deepfake audio targeting an EA with malware-laced NDAs’.
- Recent polling confirms this priority, with 22% of respondents identifying cybersecurity as their top area of security investment:

Family offices continue to prioritise cybersecurity, human risk, and succession above geopolitical or reputational risk, indicating a strong internal risk lens.
Practitioner Perspective
Kate Bright, founder of UMBRA International, points to the convergence of digital and personal risk:
“The boundary between cyber hygiene and physical safety is fading. Families need to start with awareness and build toward muscle memory.”
Peachey reinforces the need for cultural change:
“You don’t solve cyber risk with software. You solve it with systems and habits. The most secure families are the ones that rehearse, challenge assumptions, and invest in detection as much as prevention.”
Experts also note that many family offices with existing incident or disaster recovery policies fail to conduct tabletop exercises or regular updates, rendering them ineffective when an incident occurs.
Actions & Imperatives
- Designate cybersecurity as a board-level issue
Regularly review cyber risk posture and incident planning at the highest level, ensuring strategic alignment and resource allocation. - Run AI-era simulations
Include deepfakes, executive impersonation, RaaS scenarios, and vendor-led breaches in tabletop drills to test preparedness against modern attack vectors. - Map digital exposure across the ecosystem
Cover not just the family office, but household staff, travel providers, legal counsel, third-party vendors, and tech providers, implementing robust TPRM. - Develop layered response playbooks
Align cyber, legal, reputational, and communications protocols for integrated crisis handling, recognising the interconnected nature of cyber incidents. - Partner with cyber forensics and insurers
Establish relationships before an incident to improve response time, evidence preservation across cloud environments and mobile devices, and financial resilience. - Invest in continuous training and awareness
Ensure all stakeholders understand current threats, their roles in prevention, and response protocols.
What to Watch in 2026 and Beyond
Looking ahead, the weaponisation of AI in cyberattacks will undoubtedly intensify, leading to more convincing deepfakes, hyper-personalised social engineering, and autonomous attack agents capable of exploiting vulnerabilities with minimal human oversight.
At the same time, quantum computing looms as a future disruptor. While still emerging, its potential to break existing encryption standards underscores the need for long-term cryptographic agility and forward-looking data protection measures.
Furthermore, the increasing integration of operational technology (OT) in smart estates and family-owned businesses will continue to expand the attack surface, heightening the cyber-physical risks to their critical infrastructure.
Finally, regulatory environments will continue to evolve. Compliance will likely shift from a focus on basic reporting toward a demand for demonstrable threat hunting, robust incident preparedness, and system-wide resilience protocols.
4. Physical Security
When the Gate Is Digital
In early 2025, a smart-home breach at a US coastal estate allowed intruders to disable perimeter alarms and gain entry while the family was home. The breach originated from a compromised mobile app connected to gate controls and had been facilitated weeks earlier through leaked contractor access credentials. It was a physical incident triggered by digital missteps.
Strategic Context
Physical security risks for family offices in 2025 have expanded in both dimension and definition, demanding a more integrated and technologically aware strategic approach. Compared to 2024, today’s threats are overwhelmingly cyber-physical.
Traditional vulnerabilities such as unlocked gates or unvetted drivers are now critically amplified by digital exposures – from IoT-based surveillance systems and smart home devices to app-controlled estate infrastructure. A compromised email containing travel plans, for instance, is no longer just a data leak; it is a direct physical security risk.
This convergence has manifested in stark new ways, with a notable rise in global crypto-related kidnappings and extortion events, where criminals leverage stolen digital data – such as cryptocurrency wallet holdings – to launch targeted real-world physical attacks.
This is occurring as high-net-worth visibility increases. Philanthropy, political engagement, luxury lifestyles, and a pervasive online presence make families more trackable and, consequently, more vulnerable. Smart travel tools, biometric estate systems, and even casual online postings can leave exploitable digital trails that adversaries can use to facilitate physical threats such as stalking, harassment, burglary, or even kidnapping.
As Peachey states,
“The threat matrix now includes digital behaviour and real-world routines. Physical security is no longer a matter of fences and bodyguards, it is about understanding the ecosystem of exposure.”
The spectrum of threats is broad, encompassing targeted violence, extortion, travel-related dangers, and significant insider threats. Yet, preparedness often lags: fewer than half of family offices report regularly evaluating physical security risks, and periodic reassessments of staff security profiles are alarmingly infrequent (studies show only 37% periodically reassess staff, while another indicates 81% do not conduct periodic checks on all personnel).
This neglect creates significant vulnerabilities to insider threats, a risk compounded when only about half of family office personnel participate in broader risk mitigation and security training.
Modern Executive Protection (EP) is evolving beyond traditional bodyguards to a holistic, intelligence-led model integrating physical, digital, and reputational risk advisory, leveraging AI for threat detection and proactive OSINT. Experts advocate for a “Secure Lifestyle®” model, emphasising that siloed approaches are dangerous, as a digital breach can rapidly trigger reputational damage and heighten feelings of physical insecurity.
Providers such as Crisis24 have responded by offering integrated protective intelligence, estate security, and travel risk solutions, reflecting the demand for unified physical–digital response models among families with international profiles.
Damon Spencer from Accordant Global Partners confirms this trend, noting they have seen “travel patterns and device metadata used to track or surveil clients. Spencer notes that information from fitness apps, travel logs, and data brokers is increasingly being used to map personal routines and vulnerabilities, a risk that spans both cyber and physical domains.
Evidence & Indicators
- 59% of respondents in Simple’s poll agreed that physical security is “rising but under-discussed” inside their family office
- 36% reported elevated concerns about principal safety over the past 12 months
- More than 50% of new EP (executive protection) requests now include travel security, digital access audits, and protocol reviews, reflecting the cyber–physical convergence
- Confirmed rise in crypto-related kidnapping and extortion cases, explicitly linking digital asset exposure to physical threats
- Uptick in demand for biometric locks, safe house networks, and active assailant insurance, especially in the US, LATAM, and parts of Asia
- Fewer than half of family offices regularly evaluate physical security risks
- Only 37% periodically reassess staff security profiles, heightening insider threat risks
Practitioner Perspective
Kate Bright, founder of UMBRA International, highlights a critical mindset shift:
“Families are starting to understand protective living. It is not just about preventing the worst. It is about enabling the best – safely, discreetly, and with systems that support the family’s pace and preferences.”
Her approach is built on what she calls the “4 Pillar model (physical, digital, reputational and emotional security being the 4)” which aligns personal security with a family’s values and legacy.
Another contributor spoke of advances in drone surveillance and counter-surveillance appearing in private family contexts:
“We are seeing drones used to scout properties before events, and counter-drone solutions for estate perimeters. This was unthinkable just five years ago.”
Actions & Imperatives
- Modernise physical audits
Include estate IoT devices, remote access controls, smart home systems, and third-party vendor linkages in regular security assessments. - Create integrated travel protocols
Combine itinerary monitoring, redundant secure communications, geopolitical risk tiering by location or event, and cyber hygiene for travel devices. - Adopt digital executive protection
A holistic approach to protecting individuals against cyber, physical, and reputational threats stemming from their digital footprint. - Implement structured background vetting and continuous monitoring
Especially for domestic staff, contractors, and short-term hires, with periodic reassessments to mitigate insider threats. - Rehearse threat scenarios
Include active shooter, intrusion, cyber–physical breaches (e.g. hacked smart systems), and targeted protest scenarios in simulations. - Blend physical and cyber oversight
Build joint dashboards, reporting lines, or cross-functional teams to manage interconnected physical and digital risk domains.
What to Watch in 2026 and Beyond
The proliferation of sophisticated, autonomous drone technology for surveillance and potentially disruptive purposes will continue to challenge traditional physical security perimeters, necessitating advanced counter-drone measures and aerial threat intelligence.
The increasing use of biometric data for access and personalisation will create new high-value targets for attackers if not adequately secured, linking digital identity theft more directly to physical access breaches.
Furthermore, as global mobility resumes and potentially shifts due to geopolitical factors, understanding and mitigating location-specific threats – including civil unrest or targeted actions against visible wealth – will become even more critical, demanding dynamic risk assessments and adaptable security postures.
The ethical and privacy implications of pervasive surveillance technologies, both offensive and defensive, will also demand careful consideration and governance.
5. Open-Source Intelligence (OSINT)
When OSINT Turns Operational
In mid-2024, a family office in the Middle East learned of a kidnapping threat only after a journalist called to verify rumours from a public message board. The attackers had triangulated school location data, travel patterns, and philanthropic publicity using only publicly available sources – some indexed by search engines, others buried in PDF footnotes and event materials. The family had never heard of OSINT. Their adversaries had.
Strategic Context
Open-Source Intelligence (OSINT), the structured collection and analysis of publicly available information, has rapidly transitioned from a niche practice to a frontline strategic risk domain for family offices.
In 2024, its offensive use was often focused on digital impersonation and reputational slander. By 2025, the stakes have dramatically escalated. Adversaries are now adept at combining OSINT with AI-generated synthetic content, data from third-party leaks, and real-world surveillance to orchestrate sophisticated physical, financial, and reputational attacks.
OSINT is no longer a static collection of data points but a dynamic, exploitable exposure layer that underpins a multitude of threats.
Cohen emphasises,
“OSINT is no longer passive. It is the foundation of synthetic identity creation, phishing vectors, and reputational takedowns. If you’re not monitoring your OSINT exposure, someone else is using it against you.”
This is critical because a family’s reputation – a vital intangible asset influencing relationships and opportunities – is increasingly fragile in an era of rapid social media dissemination and AI-driven disinformation. Cybersecurity incidents, particularly data breaches, can instantly morph into major reputational crises. The online activities of family members, especially the digitally native Next Generation, also contribute significantly to the family’s OSINT profile and potential vulnerabilities.
Despite its critical importance, polls indicate that nearly two-thirds of family offices lack a formal OSINT strategy. Few can articulate the types of data points being indexed, mirrored, or scraped about them in real time, let alone implement effective mitigation. This is driven by a critical shift in thinking, as Linden Baker of Legendary points out, “Family offices are starting to realise that digital invisibility doesn’t equal safety anymore, in fact, an outdated online presence can raise questions and put the firm at risk.”
Experts confirm a sustained uptick in coordinated online backlash and note that AI has fundamentally changed how and where reputation manifests, diminishing traditional media’s role. Family offices must now actively monitor what AI systems “know” and “think” about them, and proactively feed these systems with substantive, accurate content.
As Michael Macfarlane notes, traditional PR approaches are increasingly ineffective in an AI-driven environment.
“Most UHNWIs are badly advised on reputation today,” he cautions, “because their advisors rely on obsolete pre-AI tools. Reputation now hinges on what AI systems understand about you, and feeding them with substantive, multi-format content is critical.”
He argues that with AI’s ability to unravel technical trickery, “SEO will become redundant”. The key, he states, is to actively “monitor what various AI’s know and think about them, and ‘feeding’ those AI with substantive content to train them into presenting an true and accurate reputation”. This proactive stance, integrating OSINT with broader reputational risk management, cybersecurity, and operational security, is vital for building resilience against bad-faith narratives and targeted attacks.
Evidence & Indicators
- 68% of recent reputation and physical security incidents were preceded by open-source reconnaissance
- Fewer than 20% of family offices reported using an OSINT monitoring or suppression service
- 47% of professionals interviewed said social media exposure is the single greatest OSINT blind spot for families
- Counter-OSINT techniques such as data scrubbing, metadata cleaning, and takedown services are becoming more widely adopted but remain inconsistently applied
- Poll data shows digital identity protection is a risk topic 24% of respondents wish to explore further, highlighting growing awareness
- Experts report a sustained rise in coordinated online backlash and AI-driven disinformation campaigns targeting UHNWIs
Practitioner Perspective
Practitioners across the intelligence field describe a fundamental mindset shift. The goal is no longer simply to erase a family’s digital footprint, but to actively curate and manage it. This involves continuously monitoring what information is publicly available, understanding how adversaries connect disparate data points, and taking proactive steps to shape the family’s digital narrative.
This involves real-time awareness of search results, impersonation attempts, fringe content, and sentiment shifts.
Peachey added:
“OSINT isn’t just about defence. It’s a way to proactively scan for threats before they escalate. It should be integrated into every security or travel plan.”
According to Linden Baker of Legendary, family offices are beginning to see digital visibility as an asset to manage, not just a liability to reduce:
“There’s a clear shift from reactive cleanup toward strategic reputation building. Reputation isn’t just about risk, it’s an asset that impacts deal flow, partnerships, and talent. Digital invisibility no longer equals safety. Being intentional, verifiable, and consistent online is now a core part of effective reputation management.”
Legendary’s Executive Shield programme reflects this shift, combining real-time digital monitoring, crisis simulation, and legal coordination. Their clients are increasingly developing narrative strategies and embedding reputation as a governance priority, not just a PR concern.
Lennard Hansen of Impetum emphasises that “successful reputation management requires scenario-based preparedness and internal dialogue, not just reactive PR.”
To explore how brand can serve as a strategic risk and influence tool, read about brand as a force multiplier.
Experts also stress that a resilient reputation is built on substance, as AI can quickly unravel mere technical trickery.
Actions & Imperatives
-
Commission a family-wide OSINT audit
Include names, addresses, known affiliations, investments, digital footprints of all family members (especially NextGen), and any previously published material. -
Monitor OSINT threats continuously
Implement real-time monitoring for mentions, sentiment shifts, impersonations, and data leakage, especially during high-visibility moments such as deals, travel, or litigation. -
Train all staff and close contacts
Educate on how everyday behaviour – naming conventions, photo uploads, social media settings, public discussions – contributes to OSINT exposure and how to minimise it. -
Use counter-OSINT measures
Employ professional scrubbing tools, content takedown requests, and footprint suppression services to actively manage and reduce the discoverable digital surface. -
Incorporate OSINT into family security and reputation management policy
Formalise how OSINT is reviewed, by whom, its integration into risk assessments, and the strategy for proactive narrative management. As Cohen explains, “It’s not just about what’s online, but how that data can be assembled and exploited. Synthesised identities, AI-driven impersonation, and metadata aggregation mean risk is no longer isolated to what you publish, it’s about what can be inferred.”
What to Watch in 2026 and Beyond
The sophistication of AI-driven OSINT analysis tools available to adversaries will continue to advance, enabling faster and more comprehensive profiling of individuals and their networks from disparate public data sources.
Expect an increase in “OSINT-to-exploit” chains, where publicly available information is directly and automatically fed into attack tools for phishing, social engineering, or even physical targeting.
The challenge will shift further from merely finding data to discerning intent and predicting threats from the noise.
Moreover, the rise of decentralised social media platforms and the “splinternet” could make comprehensive OSINT monitoring more complex, requiring new tools and techniques to track exposure across a fragmented digital landscape.
The ethical lines around OSINT collection and use – even for defensive purposes – will also likely face greater scrutiny.
6. Geopolitical Risk
When Stable Ground Shifts
A family office with long-standing manufacturing investments in a historically stable Eastern European country suddenly faces operational disruption. A nearby conflict has triggered not only supply chain delays but also a shift in domestic policy, with the host government imposing new, unexpected tariffs on foreign-owned assets to fund increased defence spending. What was once a predictable environment has become a source of significant financial and operational risk.
Strategic Context
Geopolitical risk has transcended being a niche concern for emerging market investors to become a primary disruptive force for all globally invested families. The post-WWII global order is fragmenting, leading to a more volatile and unpredictable world where the “red lines” for conflict are increasingly opaque. This instability is not confined to developing nations; countries once known for their stability are now susceptible to external economic pressures and domestic threats, resulting in regulatory unpredictability.
For family offices, this manifests in several ways. Shifting political alliances and trade tensions, such as those actively negotiated by the US, create protectionist policies that disrupt established supply chains and investment theses. Domestically, political polarisation, amplified by emerging technologies, can fuel political violence and social unrest that negatively impacts the business landscape even when not directly targeting the family.
Furthermore, as nations increase defence spending, the tax burden on private wealth and enterprise is likely to grow, making long-term fiscal and regulatory stability a prized, yet increasingly rare, commodity.
Evidence & Indicators
- 61% of family offices now factor geopolitical instability into investment strategy reviews.
- 45% report shifting allocations due to rising regional volatility or sanctions.
- 3 in 5 respondents to a Simple poll cited political unpredictability as a growing operational concern.
- Demand for geopolitical advisory and horizon scanning has grown 37% year over year among firms serving UHNWIs.
- 68% of FO professionals say supply chain resilience has now overtaken efficiency as a strategic priority.
- Growing physical threats towards wealthy individuals in some regions due to rising social and political tensions.
- More frequent and unpredictable changes to tariffs, sanctions, and foreign ownership regulations
Practitioner Perspective
Philip Mirande of Control Risks notes,
“A country where the family have assets for many years may not be stable in three to five years. The limits of geopolitical risks, or the red lines, or escalation thresholds, are becoming increasingly opaque, which can trigger a regional conflict quicker than before.”
He emphasises the need to analyse which countries can offer long-term stability and to be prepared for a world where global tensions are no longer settled primarily by diplomacy.
Actions & Imperatives
-
Integrate geopolitics into due diligence
Beyond financial metrics, assess the long-term political and regulatory stability of any country where assets, operations, or family members are based. -
Implement proactive risk monitoring
Establish a formal process for horizon scanning and strategic intelligence to anticipate political shifts, regulatory changes, and emerging threats in relevant jurisdictions. -
Build resilient structures
Diversify operational footprints and build resilience into supply chains to withstand geopolitical shocks and trade disruptions. -
Enhance personal security posture
Conduct in-depth security risk assessments for family members, particularly in regions with rising political violence or social unrest, and provide tailored security awareness training. -
Scenario plan for political change
Use scenario analysis to understand how different political outcomes – for example, major elections or shifts in foreign policy – could impact the family’s assets, operations, and reputation.
What to Watch in 2026 and Beyond
The intersection of geopolitical instability and cyber warfare will likely intensify, with state-sponsored actors targeting the private assets of influential families as a form of proxy conflict.
The “balkanisation” of the internet and technology standards – the “splinternet” – will continue, creating distinct regulatory and operational blocs that complicate global investment and data management.
Furthermore, resource scarcity, from water to critical minerals, will become a more significant driver of geopolitical tension, creating new conflict hotspots and investment risks that family offices must factor into their long-term strategic planning.
7. Regulatory & Governance Risk

When Trust Becomes a Liability
A long-serving, highly trusted financial adviser at a family office recommends a complex, high-profile investment. The family, relying on the trusted relationship, proceeds without a separate compliance review. The investment later draws regulatory scrutiny, and the lack of documented, independent due diligence creates a significant legal and reputational crisis. The incident reveals that the family’s reliance on informal, trust-based processes created a critical governance gap.
“We’re seeing a convergence,” adds Philip Mirande of Control Risks. “Geopolitical volatility, reputational scrutiny, and operational blind spots don’t happen in isolation. Sophisticated families are starting to manage these interdependencies through formal horizon scanning and scenario planning.”
Strategic Context
Perhaps the most underestimated risk for family offices in 2025 is the fundamental shift in how they are perceived. As Simple Expert and family office advisor, Oliver Yorke, highlights, family offices are increasingly being viewed as a distinct “asset class” by regulators and the public. Their growing influence in capital markets is attracting greater scrutiny, and longstanding exemptions related to transparency, beneficial ownership, and compliance are being reconsidered in jurisdictions such as the US and UK.
This places immense pressure on family offices to professionalise their internal structures, as many are not prepared for potential reporting and governance mandates that could compromise privacy and expose operational gaps.
This external pressure is compounded by internal governance vulnerabilities. The culture of trust, while fundamental, can lead to dangerous gaps in oversight, a risk that persists across staff, partners, and even family members. This creates what Cohen calls “cognitive blind spots”, making the family office vulnerable to influence through “elite network dependency” or the use of “philanthropy as geopolitical leverage”.
Discretion, when it comes at the cost of operational security, becomes a liability. This is especially true for third-party and vendor risk, where families are now compelled to move towards corporate-grade due diligence, evaluating partners not just on service quality but also on their cybersecurity posture, compliance frameworks, and reputational exposure.
For a deeper dive into how ownership frameworks can strengthen alignment and risk culture, see why an ownership strategy matters.
A lack of cross-functional coordination, where legal, compliance, and investment teams operate in silos, can make risks worse, turning manageable issues into significant crises.
The clear trend is a move towards professionalisation, with the appointment of Chief Risk Officers (CROs) becoming more common as family offices recognise the need for centralised oversight to navigate this new era of financial, reputational, and regulatory uncertainty. As Bright notes, this involves tangible steps such as appointing internal risk management liaisons , embedding risk reviews into annual governance cycles , and creating cross-functional working groups to improve coordination.
Firms like Accordant Global Partners are helping to formalise this coordination, noting that true risk maturity hinges on structure, not just tools. By embedding roles like a Chief Risk or Resilience Officer, families can assign clear domain ownership, reduce informal dependencies, and prevent cross-domain exposure.
The risk of overlooking these governance gaps is severe. Accordant shared a case where an executive assistant with ties to organised crime was able to record board meetings, concluding with a stark insight: “These are governance failures, not tech ones.”
Evidence & Indicators
- 40% of larger family offices (>$1B AUM) now have formal compliance or risk leadership roles, up from 27% in 2022.
- 49% of family offices have not reviewed governance structures in the past 2 years.
- 33% of respondents cite overdependence on key individuals as their top internal risk.
- 58% of new vendor partnerships lack documented due diligence on cybersecurity and compliance.
- Regulatory proposals targeting family offices were introduced or expanded in at least six major jurisdictions in 2024–2025.
- A clear trend of larger family offices appointing formal Chief Risk Officers (CROs) or assigning dedicated risk oversight at board level.
- An internal awareness gap, where trust in long-term employees and partners persists as a potential vulnerability.
- Anonymised cases confirm that lack of cross-functional coordination between advisory, compliance, and investment teams can escalate risks.
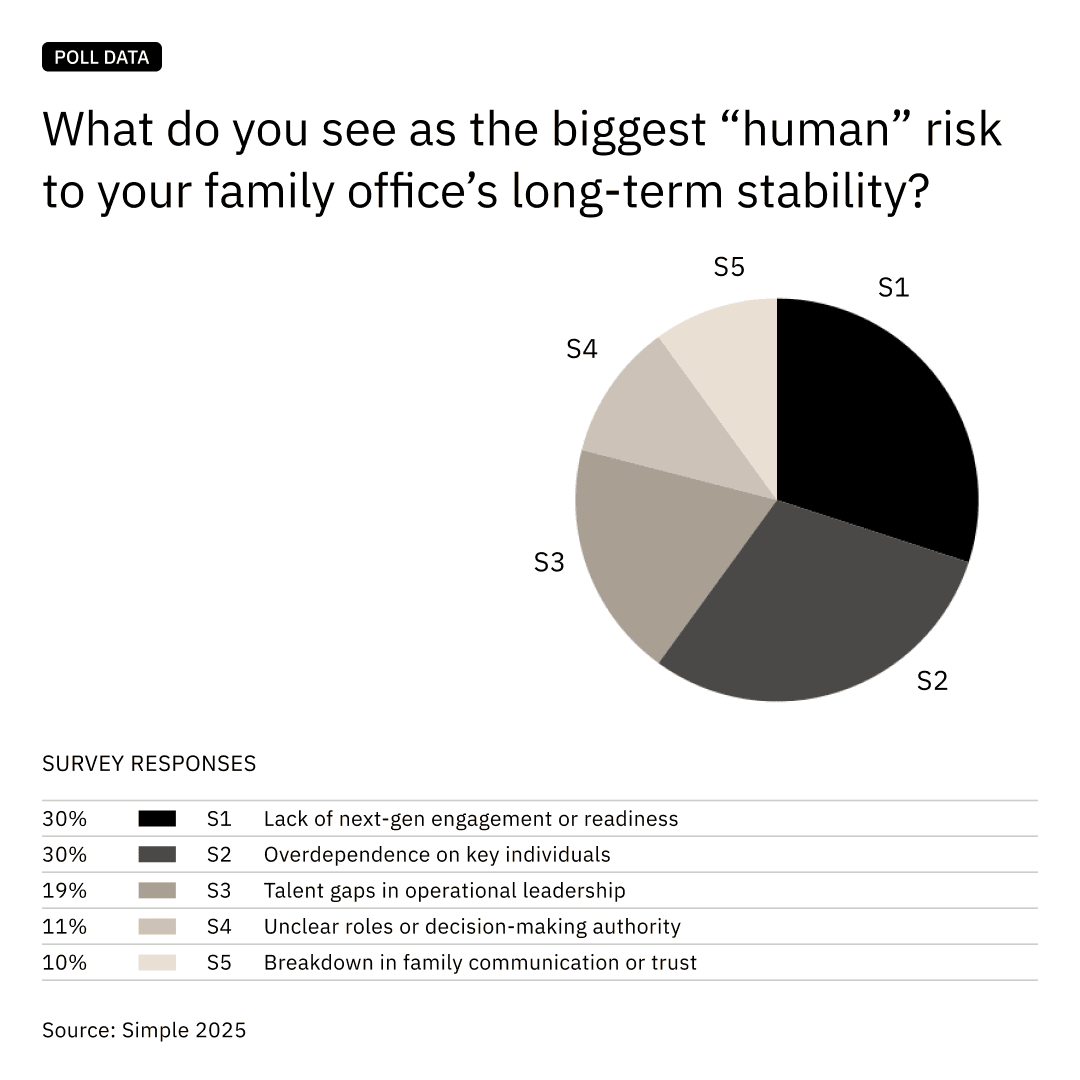
A lack of next-gen readiness, overdependence on key individuals, and unclear decision authority were identified as leading human risks to long-term family office stability.
Practitioner Perspective
Oliver Yorke states,
“Family offices are increasingly underestimating regulatory and classification risk, particularly as they become recognised as a distinct asset class… Many family offices are not yet prepared for potential reporting, disclosure, and governance mandates.”
He stresses that preparing for unknown threats means “moving from reactive to proactive,” which involves adopting modern systems and partnering with trusted third parties to build a more resilient foundation. On insider risk, he advises, “Discretion should not come at the cost of operational security.”
This need for structure without sacrificing agility is what Lennard Hansen of Impetum calls the “‘two-speed governance’ model.” He advises that:
“Implementing clear, lightweight governance for routine decisions alongside structured oversight for strategic, high-risk ventures preserves agility while managing critical risks effectively. The key misconception to avoid: good governance doesn’t slow you down; it ensures you can confidently move at pace.”
Actions & Imperatives
-
Professionalise internal governance
Establish clear protocols, formalise decision-making processes, and embed risk reviews into all complex or high-profile activities. -
Invest in in-house risk talent
Appoint experienced professionals in risk, compliance, or cybersecurity, and embed them into strategic decision-making to reduce long-term exposure. -
Implement formal controls
Mitigate insider threats by implementing role-based access to sensitive information, conducting regular internal audits, and ensuring clear protocols are followed, even in small, close-knit teams. -
Adopt corporate-grade vendor management
Structure a formal due diligence process for all third parties, assessing them on compliance, cyber posture, and reputational risk, not just service quality. -
Anticipate regulatory change
Proactively monitor the evolving regulatory landscape and begin structuring operations and governance to align with potential future compliance and reporting requirements. Philip Mirande of Control Risks underscores that “Governance isn’t just an internal challenge; it’s now shaped by rapidly shifting external expectations. From geopolitical volatility to ESG and compliance, the interdependencies are growing.” He advises families to adopt a horizon-scanning approach that integrates political, reputational, and operational signals.
What to Watch in 2026 and Beyond
The “asset class” designation will likely lead to concrete regulatory action, with multi-family offices being the first to be treated more like regulated financial entities. Expect new mandates around beneficial ownership transparency, capital adequacy, and formal compliance reporting.
The actions of a few high-profile family offices could trigger industry-wide regulatory responses, making reputational contagion a significant governance concern.
Furthermore, as family offices engage in more direct and complex investments, the potential for conflicts of interest will grow, demanding even more robust and transparent governance frameworks to manage them effectively.
8. Forensic Investigations

When Familiarity Masks Fraud
In late 2024, a European family office uncovered small but persistent treasury discrepancies. What first appeared to be accounting anomalies evolved into a multi-year internal fraud, exposed only after a forensic review of access logs and authorisations. The assistant involved had been part of the household team for more than a decade.
Strategic Context
In 2025, forensic investigations have become a key, and often critically underutilised, pillar of strategic risk readiness for family offices. Traditionally reactive and corporate-focused, forensics in the private wealth sphere must now encompass proactive oversight, robust insider threat detection, and swift crisis recovery.
The escalating sophistication of synthetic identity fraud, the proliferation of shadow IT tools within trusted circles, and the persistent risk of insider exploitation mean that trust, while essential, can no longer be a substitute for verification and structured oversight. The human element, with its inherent vulnerabilities, remains a primary concern.
Compared to 2024, there is broader – albeit still insufficient – recognition that digital breadcrumbs such as access logs, communication patterns, and financial transaction anomalies are often the first indicators of compromise or malfeasance. However, a significant gap remains: many family offices (61% in one survey) had never conducted a formal forensic review.
Furthermore, 38% acknowledged they would not know how to proceed if fraud or compromise was suspected, indicating a lack of clear protocols for escalation and investigation when discrepancies arise. This is particularly concerning given the rise in digital forensics engagements tied to business email compromise, internal access abuse, and cryptocurrency-related fraud.
Experts highlight the “grey zone”, where the inherent discretion and trust-based decision-making common in family offices can become vulnerabilities. These environments are susceptible to subtle manipulation through cognitive blind spots or exploitation of elite network dependencies.
Therefore, forensic readiness must be coupled with strategic vetting of personnel, going beyond traditional checks to understand intentions, motivations, and hidden affiliations using OSINT and human intelligence. As Oriane Cohen explains, this involves applying frameworks like MICE (Money, Ideology, Compromise, Ego) to understand the human leverage points that traditional due diligence misses. Every person is susceptible to manipulation through at least one of these dimensions, and overlooking this can expose family offices to serious strategic harm. She provides a clear example of this in action: traditional due diligence on a philanthropic partner might show their finances are clean, but strategic vetting could reveal “hidden connections to controversial political movements or questionable funding sources”.
Proactive forensic hygiene and readiness are not just about catching wrongdoing; they are about deterring it and signalling strong governance.
Evidence & Indicators
- 61% of family offices surveyed had never conducted a formal forensic review
- 38% acknowledged they would not know how to proceed if fraud or compromise was suspected
- Rise in digital forensics engagements tied to business email compromise, access abuse, and crypto recovery
- More collaboration emerging between forensic teams, legal advisers, and insurance providers, indicating a maturing approach to incident response
- Weak insider threat management is a common finding, with infrequent periodic reassessments of staff security profiles
Practitioner Perspective
Oriane Cohen emphasises early readiness:
“The longer it takes to launch a forensic review, the more evidence degrades. Families need protocols in place before trust is broken.”
This includes having forensic review teams on standby, as highlighted in real-world examples where dismissed staff exploited lax offboarding.
Peachey adds:
“Forensics used to be damage control. Now it’s part of operational hygiene. Knowing what normal looks like helps you spot the subtle deviations that signal trouble.”
This proactive stance is crucial for identifying human-driven risks.
Actions & Imperatives
-
Establish an investigative readiness plan
Define who investigates (internal or external), what events trigger action (clear thresholds), how evidence is preserved (chain of custody), and escalation paths. -
Include digital forensics in response playbooks
Cover cloud access logs, mobile devices, messaging apps, cryptocurrency wallets, and smart device data. -
Appoint or retain trusted forensic partners
Ideally external and independent from day-to-day operational teams, vetted before a crisis. -
Run proactive integrity reviews and anomaly detection
Especially after leadership transitions, key staff exits, major fund movements, or significant system changes. -
Treat forensic hygiene as a confidence signal
Reassure stakeholders – family members, board, partners – of high governance standards and a commitment to integrity. -
Integrate strategic vetting into HR processes
Implement enhanced due diligence for key roles, understanding the “human factor” beyond surface checks.
What to Watch in 2026 and Beyond
The increasing complexity of financial instruments, including digital assets and decentralised finance (DeFi) protocols, will present new challenges for forensic investigators. These will require specialised expertise and tools to trace transactions across opaque and rapidly evolving platforms.
AI will play a dual role: while adversaries may use AI to better conceal illicit activities, forensic teams will increasingly leverage AI for anomaly detection, predictive analysis of potential fraud, and sifting through vast datasets more efficiently.
The forensic challenges posed by ephemeral data – from encrypted messaging apps with auto-delete functions to volatile memory on IoT devices – will necessitate faster response times and more advanced data capture techniques.
Furthermore, cross-border investigations will likely become more complex due to diverging data privacy regulations and geopolitical tensions, making international cooperation and legal expertise even more crucial.
9. Crisis Management

When Crisis Becomes Cascading
In 2024, a politically visible North American family experienced a multilayered crisis: a ransomware attack on their foundation’s systems coincided with anonymous leaks alleging financial misconduct. With no unified crisis plan in place, the response was fragmented, resulting in media missteps, donor withdrawal, and reputational fallout that far outlasted the breach itself.
Strategic Context
The tempo, complexity, and cascading nature of crises facing family offices in 2025 have markedly accelerated, demanding a strategic shift towards institutionalised resilience. What might once have been an isolated event – a data breach, a public relations controversy, or a travel incident – is now highly likely to spark immediate and far-reaching ripple effects across operational, financial, reputational, legal, and even personal wellbeing domains.
The stakes are significantly amplified by the proliferation of AI-driven impersonation, synthetic misinformation capable of going viral across multiple platforms within hours, and the interconnectedness of global systems.
While awareness of these multifaceted risks has grown since 2024, investment in comprehensive, integrated crisis management planning and preparedness remains critically limited. As Philip Mirande notes, the most common oversight is simply the absence of a documented, formalised crisis management plan and a designated, trained Crisis Management Team. The informal, undocumented processes that arise from a family-driven culture are no longer sufficient in the modern risk environment.
Data reveals significant preparedness gaps: large percentages of family offices lack formal cyber incident response plans, disaster recovery plans, geopolitical contingency plans, or even basic business continuity frameworks. Spencer of Accordant shared a powerful anecdote illustrating this gap – a family “had insurance, but no working plan when an FO staff member had a medical crisis abroad”.
This lack of preparedness itself constitutes a major risk, leaving them highly vulnerable to severe consequences including financial losses, operational downtime, lasting reputational harm, eroded trust, and legal or regulatory penalties.
Experts emphasise that effective crisis management requires moving beyond fragmented planning towards an integrated, all-hazards resilience framework. This involves not just developing a plan, but embedding resilience through rigorous training, realistic simulations (which often reveal crucial misalignments in protocols), and regular updates. Building “muscle memory” for crisis response is essential.
The ability to activate a coordinated response using pre-established, multidisciplinary partners – including legal counsel, forensic specialists, crisis communications, and security advisors – is increasingly essential. The most resilient families invest early in these relationships, ensuring they are not sourcing support mid-crisis but operating from a well-practised playbook. Some families are also recognising that litigation itself can be a reputational attack vector. As Michael Macfarlane notes, “the real battleground is no longer the courtroom, but the online world, where clients face pressure to defend their position against AI-fuelled narratives long before a legal outcome is reached.”
As the concept of a Chief Resilience Officer (CRO) gains traction, so too does the expectation for integrated readiness. Firms like Crisis24 are responding by offering embedded global capabilities – medical support, threat intelligence, cross-border logistics – demonstrating the shift toward truly holistic, real-time crisis infrastructure.
Accordant Global Partners stresses the importance of operational realism, sharing a case where “a Taiwan conflict scenario exposed gaps across logistics, liquidity, travel fallback, and comms leading to an overhaul of asset and mobility planning.” This highlights how stress-testing plans against real-world events can reveal critical, unforeseen gaps.
The most resilient families invest early in these relationships, ensuring they are not sourcing support mid-crisis but operating from a well-practised playbook. As Bright highlighted with the example of one family turning a “reputational crisis into a story of resilience”, because their foresight meant they already had a “pre-agreed Secure Comms plan, a support strategy for the Principal, and a forensic review team on standby”.
This aligns with Simple’s poll data, where one in three respondents selected operational risk modelling as the topic they most want to explore further:
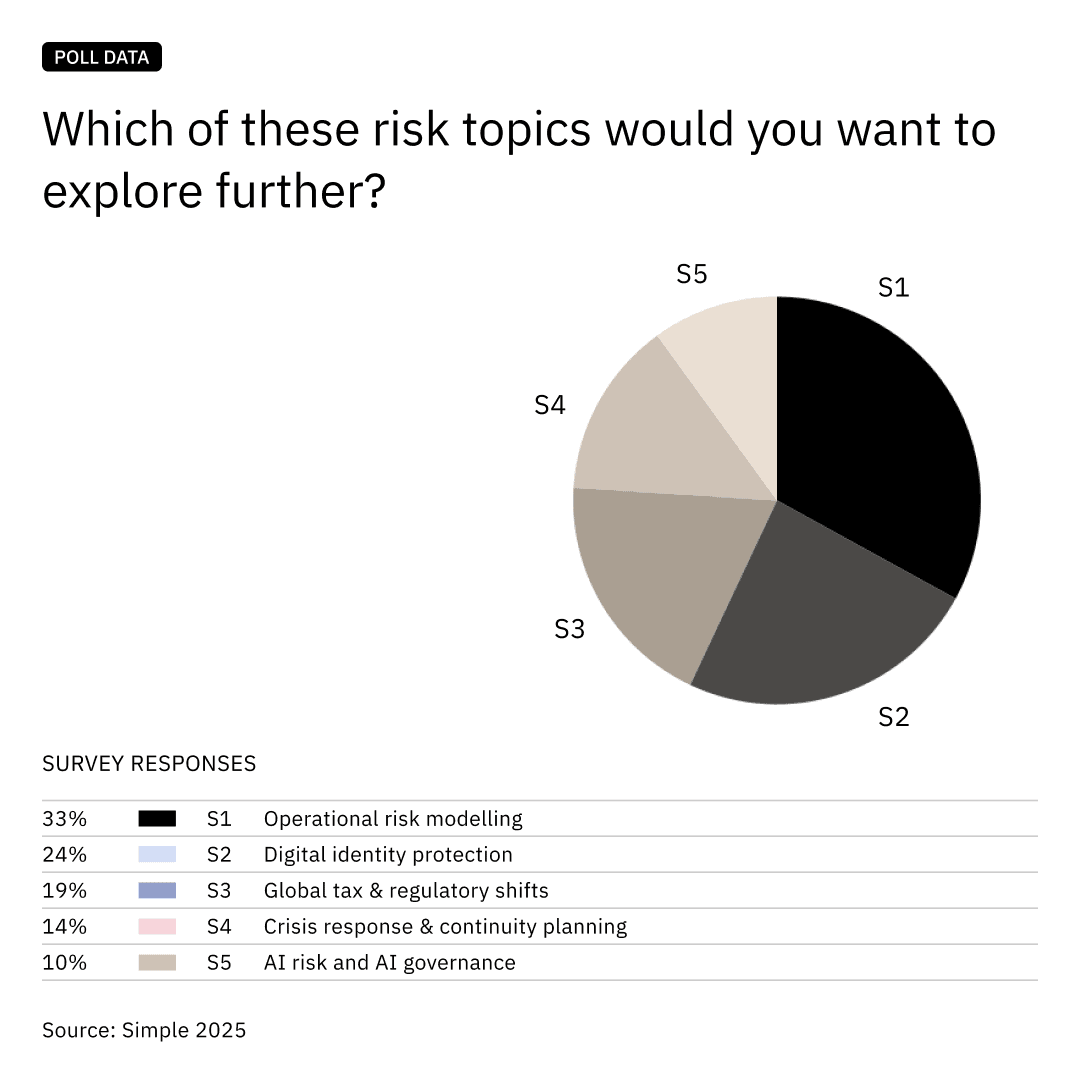
Operational risk modelling and digital identity protection top the list of topics that family offices want to explore further, underscoring the appetite for better tools and frameworks.
Evidence & Indicators
- Only 24% of family offices surveyed have a documented and tested crisis plan
- Nearly 50% reported experiencing a major incident in the past two years that would have benefited from one
- Growing demand for embedded Chief Resilience Officers (CROs) or outsourced red-team planning
- More families incorporating legal, cyber, and PR partners into annual risk simulations, though this is not yet standard practice
- Significant gaps persist in cyber IRPs (31% have none), disaster recovery plans (50% lack one), and geopolitical contingency plans
- Operational risk modelling is the top desired topic for further exploration (33% of poll respondents), indicating a need to better understand and plan for disruptions
Practitioner Perspective
Bright reframes the issue:
“Crisis response isn’t just about stopping damage. It’s about enabling secure decision-making when the stakes are high. Families who train for chaos make better calls when it counts.”
This includes having emotional resilience strategies alongside physical and cyber planning. This aligns with Bright’s Secure Lifestyle® framework, which includes emotional resilience as a core risk pillar alongside digital and physical security.
Explore the role of health in holistic preparedness in integrating healthcare into security.
Michael Macfarlane of Michael Macfarlane Associates adds:
“The families that handle crisis well treat resilience like a discipline. That means scenario planning, clear roles, and post-event reviews, not just hoping you get it right on the day.”
Demonstrating this, one multi-family office facing a collective legal dispute effectively navigated the crisis because their pre-existing management protocol and clear governance framework allowed them to respond with integrity and consistency.
Actions & Imperatives
-
Build a multi-hazard crisis playbook
Cover cyber, physical, legal, reputational, succession, and health-related events. -
Assign clear decision authority and escalation roles
Reduce confusion and improve response speed under pressure by pre-defining who does what. -
Conduct regular, realistic simulations and tabletop exercises
Include worst-case, “grey zone” scenarios – for example, misinformation plus breach plus regulatory inquiry – to test plans and build muscle memory. -
Pre-vet and integrate critical partners
Establish relationships and protocols with legal counsel, cyber forensics, crisis communications firms, security providers, and emergency logistics support before a crisis – especially for families operating across borders. -
Integrate crisis readiness into governance frameworks
Ensure values, protocols, and accountability align, potentially appointing a dedicated risk or resilience lead. -
Develop a proactive reputational resilience strategy
Build a strong, positive narrative and have pre-prepared communication elements for various scenarios.
What to Watch in 2026 and Beyond
The speed at which AI-generated misinformation and deepfakes can create and escalate crises will demand even faster detection and response capabilities, potentially requiring AI-powered tools to identify and counter synthetic media campaigns in near real time.
“Crises-as-a-service”, where threat actors offer to orchestrate reputational or operational disruptions for a fee, may become more prevalent. The impact of “grey zone” crises – those that do not fit neatly into existing categories or involve ambiguous actors and motives – will likely grow, testing the adaptability of crisis plans.
Furthermore, the increasing focus on Environmental, Social, and Governance (ESG) factors means that crises related to a family’s investments, philanthropic activities, or supply chains could have more significant and immediate reputational and financial repercussions, necessitating broader stakeholder mapping and communication strategies.
The ability to manage the emotional impact of a crisis on family members and key staff will also gain recognition as a critical component of overall resilience, what some experts refer to as the ’emotional pillar’ of a truly secure lifestyle.
10. Conclusion & Outlook
Convergence of Risks & the Need for Evolution
The sections in this report – from cybersecurity and physical safety to OSINT, forensic investigations, and crisis management – reflect an important shift for family offices in 2025: risks are not isolated, but deeply interconnected and rapidly converging.
A cyber breach can trigger a physical security vulnerability. A geopolitical event can create regulatory and reputational fallout. Any single incident can quickly escalate into a multifaceted crisis. As threat vectors evolve in tandem, they demand coordinated response systems, integrated oversight, and increasingly multidisciplinary teams.
The era of siloed risk management is over. A holistic, strategic approach is now imperative for survival and continued success.
Practitioners across the Simple network consistently emphasised that the next frontier for family offices is not necessarily more privacy – it is smarter exposure management and enhanced resilience. Hansen calls this the shift toward ‘two-speed governance’, lightweight oversight for routine issues, structured safeguards for high-stakes decisions, ensuring agility without losing rigour. He stresses the key misconception to avoid: “good governance doesn’t slow you down; it ensures you can confidently move at pace.”
That means deeply understanding the family’s digital footprint, its reputational narrative in an AI-influenced world, its internal governance gaps (particularly concerning human factors and insider threats), and its true, tested readiness to respond effectively under extreme pressure.
As Accordant Global’s Damon Spencer notes, strong governance is no longer about documentation alone, it’s about culture, ownership, and active practice. Families that treat risk as part of daily operations, not a crisis add-on, are proving the most resilient.
Overarching Themes
-
Integration is essential
The strongest family offices are breaking down silos between cyber, physical, reputational, operational, and geopolitical risk, adopting enterprise-wide risk management frameworks. -
Technology is a dual force
AI, automation, and cloud platforms have expanded capability and efficiency, but have equally broadened the attack surface and the sophistication of threats. -
Crisis is a matter of when, not if
With many threats accelerating simultaneously and converging, purely reactive plans are no longer sufficient. Proactive resilience-building is key. -
Governance is security
Those with clear roles, robust data hygiene, strong internal controls, values-based protocols, and a commitment to ongoing training are better equipped to adapt and respond. -
The human factor is paramount
Vigilance against insider threats, coupled with strategic vetting and fostering a strong security culture, is as crucial as technological defences. -
Peer networks are maturing
Expert sharing, collective benchmarking, and collaborative preparedness initiatives are becoming the new norm as families recognise shared challenges.
Looking Ahead
The professionalisation of risk management within family offices is set to accelerate. We can expect to see more appointments of Chief Risk Officers (CROs) and specialists embedded across family and enterprise structures, with advisory models like Accordant Global’s showing how families can bridge internal gaps while building long-term resilience.
This drive to professionalise is largely a response to new technological forces, especially as artificial intelligence reshapes both sides of the risk equation. While AI creates new threats like deepfakes and advanced phishing, it also offers powerful tools for detection and defence, making fluency in its dual nature essential for any adaptive family office.
To manage these emerging digital threats effectively, real-time threat visibility through proactive intelligence will become the new benchmark for security. Best practice will be defined by the use of continuous OSINT alerts, dark web monitoring, breach simulations, and predictive analytics.
Beyond technology, the very concept of security is expanding to include the convergence of narrative and safety. As storytelling and digital resilience become inseparable, managing the family’s public and private presence will be recognised as a critical component of its security posture.
This holistic approach supports a fundamental shift in mindset, where investment in resilience is treated as an asset class. Forward-thinking families will see spending on security not as a mere cost, but as a strategic investment in the preservation of wealth, reputation, and legacy.
See how this strategic mindset is shaping capital deployment in Clockwork’s 2025 Outlook.
In the end, all these strategies depend on making internal expertise a core priority. As Oliver Yorke advises, the most crucial investment is in dedicated, in-house risk and governance talent who are empowered to oversee threats and influence strategic decisions, thereby drastically reducing long-term exposure.
Postscript
This report is designed to support clearer thinking and more coordinated action around risk. As the landscape shifts – through AI, geopolitical volatility, regulatory scrutiny, and reputational exposure – family offices are re-evaluating how they manage complexity across domains.
For some, this means building internal capabilities. For others, it involves working more closely with trusted providers or strengthening governance frameworks.
In all cases, the goal is the same: to make better-informed decisions, reduce blind spots, and align protection with long-term purpose.
Security and resilience are not static outcomes. They are continuous processes that evolve alongside the family and its ambitions.
11. Acknowledgements
We extend our sincere thanks to the many experts and practitioners who contributed their time and rich insight to this report. Their frontline perspectives were invaluable in shaping its analysis and recommendations.
- Kate Bright (UMBRA International)
- Oriane Cohen (OC Strategic Advisory)
- Michael Macfarlane (Michael Macfarlane Associates)
- Philip Mirande (Control Risks)
- Linden Baker (Legendary)
- Lennard Hansen (IMPETUM)
- Morten Peachey (coc00n)
- Oliver Yorke (Simple Expert)
- Damon Spencer (Accordant Global Partners)
- Crisis24 Private Strategic Group
12. Sourcing
Select Sources
The insights and data in this report were informed by a wide range of public and private sources, including proprietary Simple polling, targeted surveys, and interviews with subject matter experts and practitioners from across the risk and security landscape. The following list represents a selection of the key public reports and analyses that provided foundational data.
Cybersecurity & Technology Risk
- Deloitte, The Family Office Cybersecurity Report, 2024.
- Kiteworks, 2024 Cybersecurity and Compliance Landscape: 50 Critical Statistics Shaping Our Digital Future.
- Munich Re, Cyber Insurance: Risks and Trends 2025.
- BlackCloak, Cyber Attacks on High-Net-Worth Individuals Will Increase in 2025.
Family Office Operations, Governance & Investment Strategy
- RBC Wealth Management & Campden Wealth, The North America Family Office Report 2024.
- UBS, Global Family Office Report 2024.
- Deloitte, The Family Office Insights Series – Defining the Family Office Landscape, 2024.
Physical Security, Geopolitical & Crisis Management
- Dentons, Evolving Risk Landscape For Family Offices – Dentons Study.
- Control Risks, The Top 10 Digital Risks for Organisations in 2025.
- Global Guardian, Family Office Safety: 5 Current Risk Factors You Need to Know.
Regulatory & Compliance
- Morgan Lewis, 5 Evolving Concerns for Family Offices in 2025.
- UHY, Key Provisions of the SEC Cybersecurity Disclosure Rule.
Additional Supporting Data
- Control Risks, Family Offices and the Age of Geopolitical Risk, 2025.
- Campden Wealth, Family Office Investment Shifts and Risk Awareness, 2024.